+91-9958 726825
Investigating Data Poisoning Attacks on Cyber-Physical Systems in Smart Grids (SCM) Using Edge Computing with Blockchain and DL-Driven Advanced Approach
|
The increasing integration of smart technology in vital infrastructures, such as smart grids, raises serious concerns about their vulnerability to cyber assaults. In this study, data poisoning attacks against Cyber-Physical Systems (CPS) in smart grids are examined, with a particular emphasis on the Smart Grid Management (SCM) component. The research suggests a complex defence system that makes use of blockchain, edge computing, and an advanced deep learning (DL) strategy. Through the reduction of latency and improvement of system responsiveness, the integration of Edge Computing seeks to improve real-time processing capabilities at the network's edge. To create a distributed ledger that is safe from tampering and maintains data integrity throughout the smart grid, blockchain technology is used. Using machine learning to detect and eliminate possible risks, the DL-driven advanced strategy focuses on anomaly detection and mitigation. The study looks at possible weaknesses in SCM and evaluates how well the suggested defence method works to prevent data poisoning attacks. The research intends to highlight the significance of a comprehensive cybersecurity strategy for smart grids by offering insights into the resilience of the suggested solution in real-world settings via simulations and tests.
|
|
Currently, vast amounts of data are generated each moment as a result of the pervasive utilisation of automation, social media, and technological devices. Concurrently, there is a rise in cyberattacks, encompassing data breaches and identity theft. A variety of security measures mitigate these threats. Within the domain of the internet and digitalisation, blockchain technology represents an emerging trend that provides superior security. The current security protocols rely on centralised servers and systems. The drawbacks of the situation encompass dependence on trustworthy third parties, susceptibility to security breaches, and singular points of failure. Conversely, blockchain technology functions as a decentralised system that depends on trust among network nodes rather than on reliable external entities. The initial digital currencies that rendered blockchain technology accessible were Bitcoin, Ether, and Ripple. Blockchain technology can achieve ethics, accessibility, and privacy standards across various industrial applications, such as banking, healthcare, supply chain management, and voting, without depending on a singular authority.[1][2][3].
The fourth industrial revolution, also known as a technological revolution, has emerged from the integration of digital technology from the previous industrial revolution with the physical and biological realms.[4][5][6][7] The advanced technologies of the fourth industrial revolution, which amalgamate individual ICT with scientific methodologies, facilitate disruptive innovation. Examples of these technologies encompass genetic editing, autonomous vehicles, 3D printing, and the Internet of Things (IoT). Considering the limitations of depending solely on internal business information in a dynamic environment, integrating external knowledge may improve a company's innovation performance.[8][9]. The comprehensive strategy for managing innovation, known as "open innovation," involves systematically promoting and identifying a diverse array of internal and external sources for innovation opportunities, actively integrating this exploration with organisational resources and capabilities, and extensively utilising those opportunities through various channels.[10][11][12][13]. Artificial intelligence profoundly impacts the industry's approach to innovation. Blockchain technology could facilitate the viability and broader adoption of open innovation by enhancing intellectual property management, increasing transparency, fostering knowledge sharing, and enabling collaborative empowerment through smart contracts and open data, alongside providing novel liquidity for funding innovation, in contrast to the fragmented nature of open innovation. With appropriate data and intelligent contracts, these technological opportunities are attainable.
Figure 1 : Attacks Categories on AI
Figure 2 : Attack Target areas in AI implementation
Smart grids are essential for modernising the electricity infrastructure and enhancing productivity, reliability, and ecology. As electrical grids become increasingly interconnected, they become susceptible to various cyber hazards, particularly information poisoning attacks. This article examines the significance of studying data poisoning attacks on Cyber-Physical Systems (CPS) within intelligent grids and proposes a novel approach that integrates edge computing, blockchain-based technology, along with deep learning to enhance cybersecurity protocols. The essay also examines the importance of analysing data poisoning attacks on cyber-physical systems in smart grids. |
|
Experimental setup
Executing the prediction algorithm on Linux-based edge-embedded boards enabled us to replicate the edge computation environment of the smart grid. The central processing unit (CPU) of these boards typically comprises a Cortex-A7, operating at 1.2 GHz, with 256 MB of RAM and 512 MB of ROM. The data was processed using the mathematics, pandas, sklearn, and numpy libraries, and the experiments were conducted in Python. The statistical gradient descent (SGD) linear regression model, which emulates the behaviour of a dynamic model in an artificial intelligence (AI) edge environment, is the designated model for this experiment. The primary criteria for evaluation are the execution duration of the attack, loss over time (LOT), and mean squared error (MSE) loss. Utilising the compromised model to predict the test set samples facilitates the calculation of the MSE loss. Subsequently, the difference between the expected values and the actual values is calculated. The duration of an assault is defined as the interval from the initiation to the conclusion of the attack. The maximum mean squared error (MSE) divided by the total duration of an attack is one method to ascertain the level of threat (LOT). In evaluating the attack's efficiency regarding time overhead, LOT provides a more comprehensive analysis than the MSE statistic. The OptP method, a conventional offline poisoning attack strategy, has served as the foundation for numerous investigations, rendering it highly representative. Data set The open power dataset, which was produced from the combined cycle power plant dataset, consists of 9568 data samples acquired between 2006 and 2011. Aside from the average ambient temperature, pressure, and relative humidity, the characteristics also include the exhaust hoover and hourly temperature, with the anticipated label being the net energy production per hour. In order to simulate the appearance of real-time data streams, we followed the steps outlined in and inputted these samples in batches. The possible range of features and labels is [0, 1] because we normalised all the sample values. The features and labels maintained a constant range of values thanks to this normalisation process. Basic parameters settings We used 5%, 10%, 15%, and 20% poisoning rates to pollute the creek. Studies conducted in the past seldom contained poisoning rates over 20%. We utilised 0.001 as the convergence termination criterion for the algorithm. We updated the characteristic scores for the contaminated point samples align with the direction of gradient increase using a decay parameter (alpha) of 0.01. |
|
Wang et al.[30] offer an authentication approach based on transfer learning empowered blockchains (ATLB) in order to preserve anonymity in industrial applications. By transferring locally or across regions, ATLB lowers the amount of time needed for model training and adds a transfer learning-based authentication method.
Salim et al.[31] hand over authentication (HO-Auth) strategy builds a user profile-based system for instant authorization and uses deep learning (DL) to authenticate devices. By ensuring that data from legitimate devices reaches the blockchain decentralised networks, the technique shields cloud applications against corrupt data. The suggested approach distinguishes between the malicious user and the truthful one by examining the CSI movement pattern gathered from many receivers. Gaur et al.[32] suggest an authentication system that classifies medical data using the SVM model before storing it in a blockchain-based ledger system in the context of e-health. The authentication procedure may be automated using smart contracts, doing away with the need for a central authority. Hammad et al.[33] combine preprocessing, feature extraction, and classification into a single unit for lower latency and cost effectiveness Using edge computing servers. Hussain et al[34] intelligent control medical authentication system makes use of DL models for face recognition in healthcare settings, including ResNet-50, VGG-16, and the local binary patterns histogram (LBPH) method. Hayashi and Ruggiero[35] presented an activity recognition model using the SVM algorithm is for automatic session management in smart home applications. Finally, provide a multi-phase method using deterministic trust transfer protocol (DTTP) to accomplish safe data transmission and use biometric technologies to identify intruders. |
|
Finally, this study tackles the important problem of cyber-physical system data poisoning in smart grids, namely in the Smart Grid Management (SCM) space. A complete defence mechanism to strengthen the resilience of smart grids against growing cyber threats is offered by integrating Edge Computing, Blockchain, and an innovative strategy powered by deep learning. By integrating Edge Computing, the system's real-time data processing capability is improved, minimising latency-related threats. By using blockchain technology, data integrity and immutability are guaranteed, avoiding unwanted tampering and creating a transparent and reliable operating environment for smart grid systems. With its emphasis on anomaly detection and mitigation, the DL-driven advanced method provides an adaptable layer of defence that can change and adapt to fight new threats. The efficiency of the suggested defence mechanism is assessed by comprehensive simulations and tests, providing insightful information about its performance in many settings and practical applicability.
Findings of the study
The findings of this study support ongoing efforts to secure and future-proof these systems against cyber threats, ensuring the dependability and resilience of our energy infrastructure in the face of a constantly changing digital landscape. Smart grids continue to play a crucial role in modernising energy distribution systems |
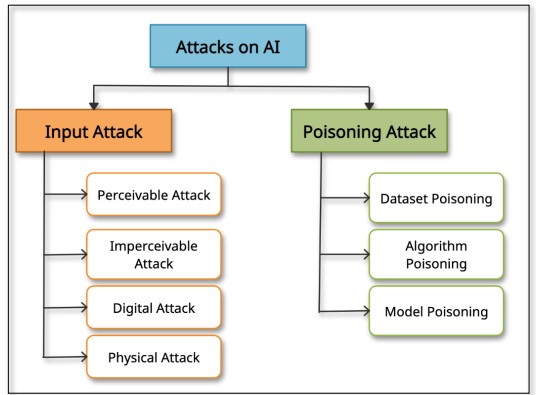 Figure 1 : Attacks Categories on AI |
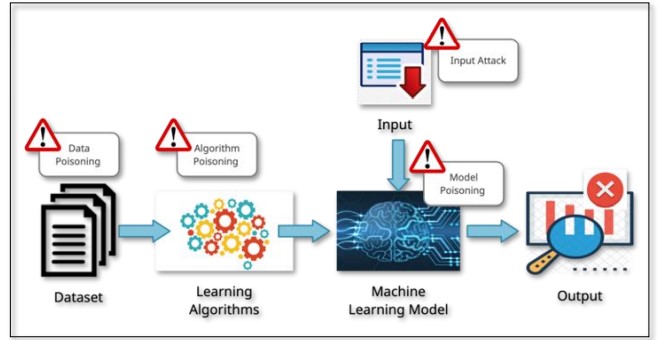 Figure 2 : Attack Target areas in AI implementation |
 Figure 3 : MSE comparison of attacks |
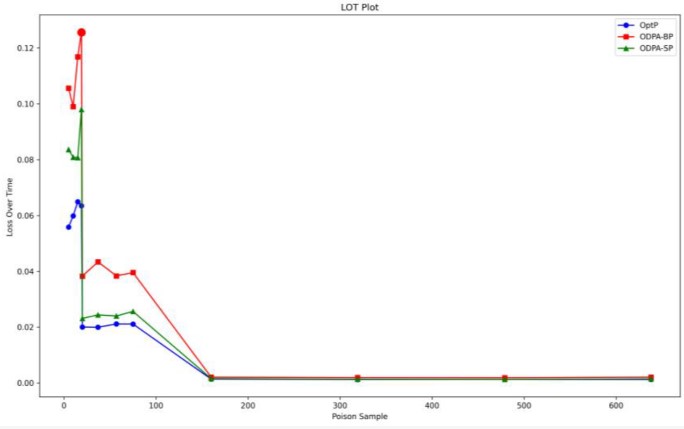 Figure 4 : LOT competition of attacks |
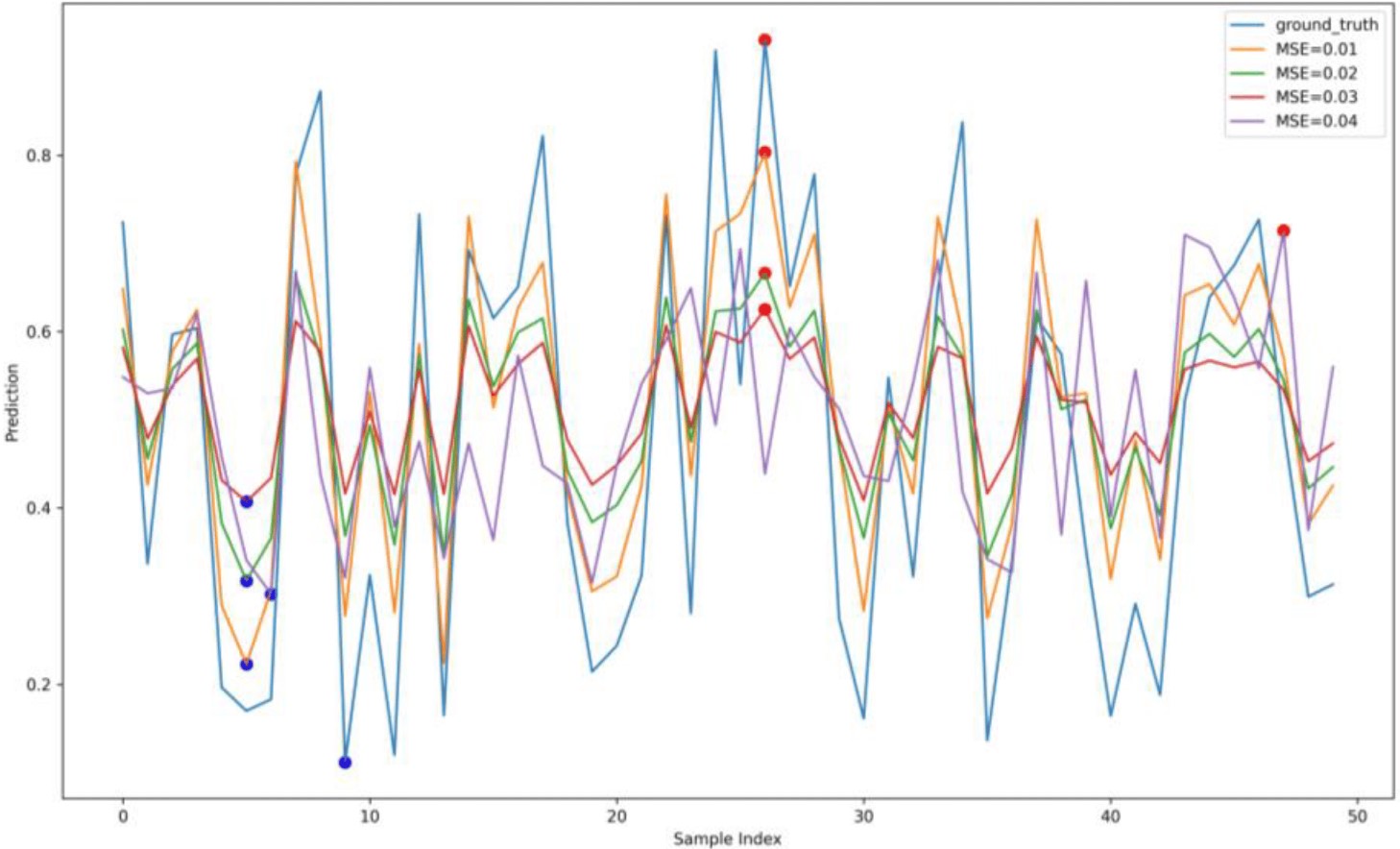 Figure 5 : Poisoning attacks impact on power prediction |
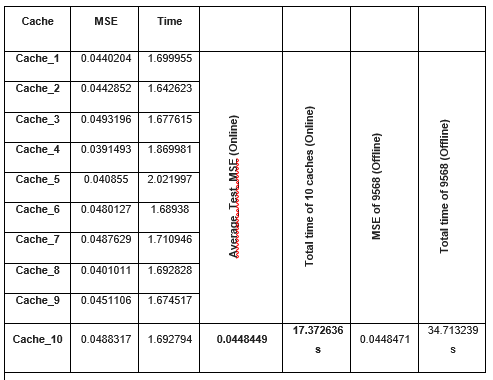 Table 1 : Online and offline poisoning attacks comparison |
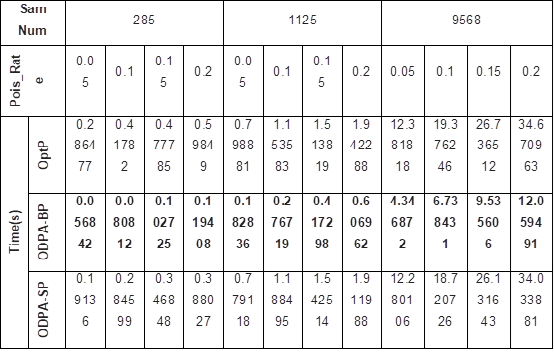 Table 2 : Three attacks Time comparison |
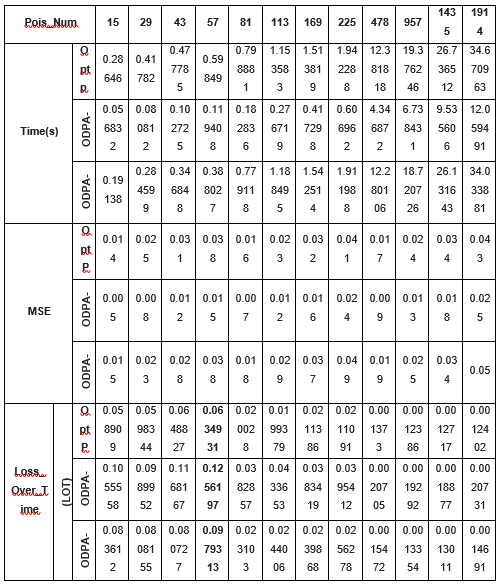 Table 3 : Comparative study of three attacks |
Fateh Bahadur Kunwar, Rakesh Kumar Yadav, , Hitendra Singh (2025), Investigating Data Poisoning Attacks on Cyber-Physical Systems in Smart Grids (SCM) Using Edge Computing with Blockchain and DL-Driven Advanced Approach. Samvakti Journal of Research in Information Technology, 6(1) 34 - 54.





